ZK Vanguard catches zero-knowledge circuit bugs before deployment
Static analysis engineered for ZK circuits. Detects private input leakage, unconstrained signals, and witness-constraint mismatches automatically, among others.

Automated detection with mathematical precision
CI/CD Friendly
Integrates seamlessly into development pipelines. Run on every commit. Get vulnerability reports in GitHub Actions. Continuous monitoring prevents regressions.
Advanced Vulnerability Triage
Related findings grouped together. Mark root causes to eliminate false alarms in bulk. Review takes minutes, not weeks.
Custom Detectors

Write detectors for patterns specific to your circuits. Custom query language for project-specific analysis. Reusable across multiple ZK projects.

Precision-Tuned Analysis
Built specifically for zero-knowledge circuit semantics. Understands constraint systems and witness generation. Detects vulnerabilities unique to ZK circuits.
Detection capabilities
Some examples of ZK Vanguard vulnerability coverage
Underconstrained Signals
Signals with insufficient constraints to uniquely determine values. Detects partially constrained and completely unconstrained signals. Enables proof forgery attacks.
Private Input Leakage
Private inputs exposed through constraint relationships and witness computation. Detects when witness values leak information. Preserves zero-knowledge property.
Compute-Constrain Difference
Discrepancies between witness computation and constraints. Identifies when witness generation implements different logic. Prevents subtle soundness bugs.
Signal-Dependent Control Flow
Witness generation that produces different outputs. Randomness in computation. Flags witness generation that is difficult to properly constrain.
Unused Fields
Circuit components instantiated but never used. Dead code in constraint systems. Wasted proving time and circuit complexity.
Out-Of-Range Signals
Discrepancies between intended value range of expressions and their enforced range based on common patterns of constraint and witness generation.
Static analysis engineered for ZK circuits
Pattern Recognition
Detectors encode common ZK vulnerability patterns. Analyzes both witness generation and constraint code. Analyzes both witness generation and constraint code to identify vulnerabilities anywhere in the ZK circuit.
Flow Analysis
Traces signal dependencies through circuits. Detects unused signals and components. Identifies potential private input leakage through constraint relationships and witness generation.
Formal Methods Foundation
Built on formal methods research. Stronger guarantees than heuristic tools. Fewer false alarms than competing analyzers.
Encode ZK expertise into reusable detectors
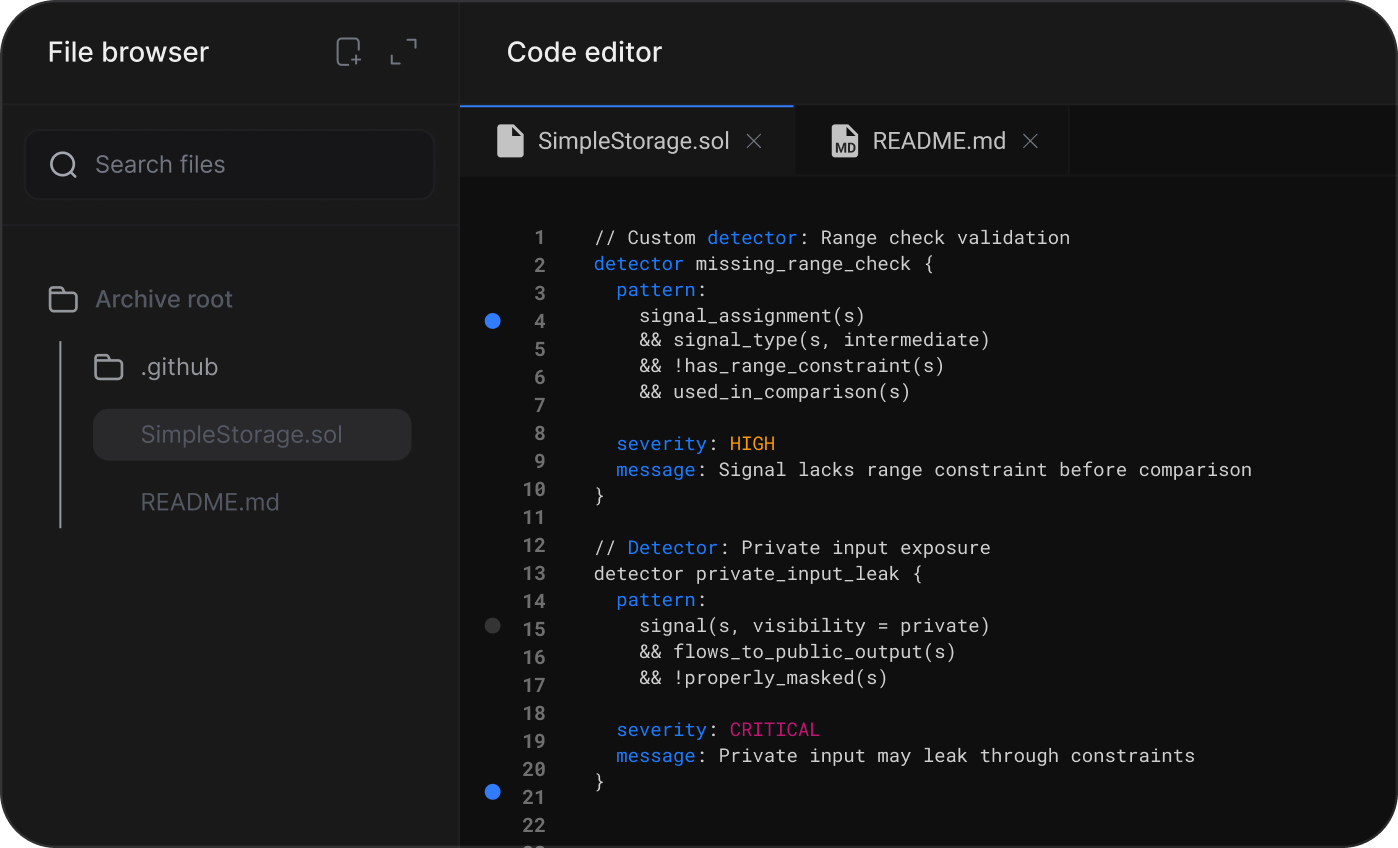
Transform circuit-specific patterns into automated detectors. Capture institutional ZK knowledge. Reusable across all your ZK projects.
Your team’s ZK security expertise becomes automated infrastructure.
Built for ZK developers
Early-Stage Safety
Catch critical ZK vulnerabilities during development. Avoid redesigning circuits after audit findings. Fix bugs when they’re cheapest to address.
Pre-Audit Verification
Run ZK Vanguard before formal audits. Reduce audit findings and costs. Demonstrate thorough security analysis to auditors.
Regression Protection
Automatically verify patches don’t introduce new bugs. Run on every circuit modification. Continuous security in CI/CD pipelines.
Comprehensive ZK security
ZK Vanguard
Static Analysis
Detects a wide range of ZK vulnerabilities. Private input leakage. Unused signals. Non-deterministic witness code. Witness-constraint mismatches. Divide-by-zero errors.
Picus
Formal Verification
Proves circuit determinism with mathematical certainty. Detects under-constrained bugs with formal guarantees. Provides proof that the same inputs always produce the same outputs.

Frequently AskedQuestions
What ZK languages does ZK Vanguard support?
2X Vanguard supports any ZK language that can be compiled into the LLZK intermediate representation. Currently, supported languages include Circom, Halo2, Zirgen, and Plonky3
How do I integrate ZK Vanguard into my workflow?
ZK Vanguard runs through the AuditHub platform. Upload your circuits, select detectors, and receive vulnerability reports. Integrates with CI/CD for continuous verification.
How does ZK Vanguard handle false positives?
Related findings are grouped together in AuditHub. Mark one root cause to eliminate false alarms in bulk. Detectors are calibrated to minimize noise. Review process takes minutes, not weeks.
How is ZK Vanguard different from other ZK analysis tools?
ZK Vanguard performs deep ZK-specific static analysis using a growing set of custom detectors. Unlike generic tools, it understands zero-knowledge circuit semantics. Detectors encode real-world ZK vulnerability patterns from extensive audit experience.
How long does analysis take?
Analysis completes in seconds to minutes depending on circuit complexity. Fast enough for CI/CD integration. Run on every commit without slowing development.
Which detector should I use first?
Start with underconstrained signals and compute-constrained difference detectors. These catch the most critical vulnerabilities. Add specialized detectors as you understand your circuits better.
Catch ZK bugs before deployment
Static analysis built specifically for zero-knowledge circuits. Integrate in minutes.
Get started in 30 minutes / No setup required / See results immediately