OrCa finds deep bugs through thousands of targeted test cases
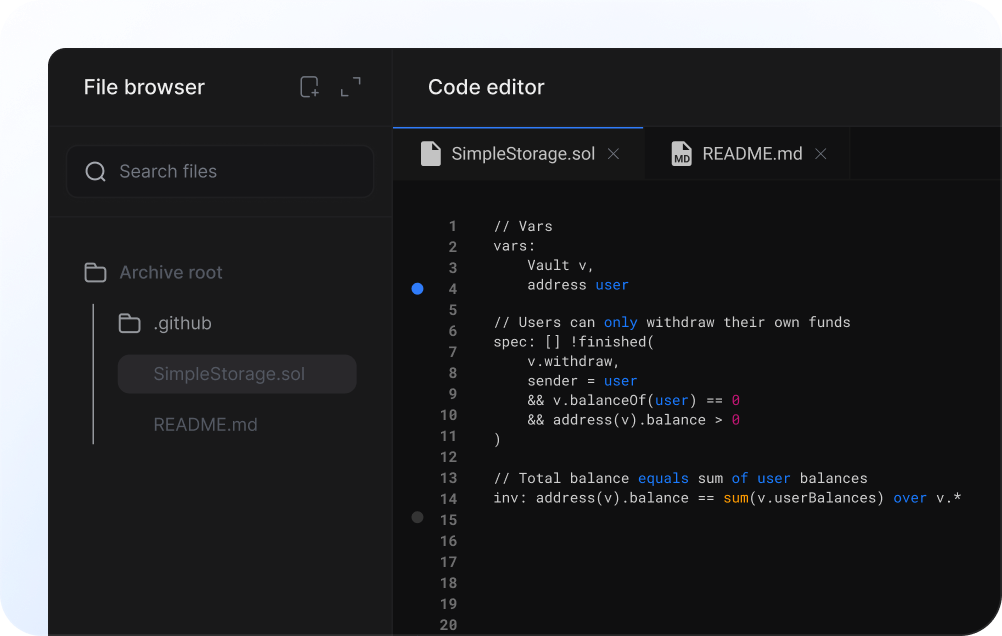
Specification-guided fuzzer for smart contracts. Write temporal properties in [V] language, let OrCa generate thousands of test cases automatically.

Intelligent code exploration
Specification-Driven Testing
Write temporal properties in [V] language. Describe what should happen, or what shouldn’t. OrCa explores thousands of transaction sequences to find violations.
Multi-Contract Fuzzing
Test complex interactions between multiple contracts. Explore DeFi protocol edge cases. Discover vulnerabilities in contract compositions, not just individual contracts.
Concrete Counterexamples
Every violation returns exact inputs and execution traces. No guesswork required. Reproduce bugs immediately with concrete transaction sequences.
Built-in Specification Library
Pre-built specifications. Start testing immediately with battle-tested templates. Automatically detect bugs across standard protocols.

Formal methods for smart contract security
Temporal Properties
Express properties that must hold over time. Define relationships between transactions. Specify invariants that should never be violated across any execution sequence.
Intelligent Exploration
OrCa generates targeted test cases based on your specifications. Explores state space systematically.
Actionable Results
Concrete counterexamples with full execution traces. Protocol behavior statistics reveal unexpected patterns. High value, no noise.
Built for complex protocols
DeFi Protocol Testing
Test lending protocols, DEXes, and yield strategies. Verify complex multi-contract interactions. Find edge cases in liquidity pools and oracle integrations.
Governance Systems
Verify voting mechanisms and proposal execution. Test timelock constraints. Ensure quorum requirements across all scenarios.
Token Economics
Validate supply mechanics and distribution rules. Verify burn and mint constraints. Test staking and reward calculations.
Access Control Validation
Ensure privileged functions remain protected. Detect authorization bypasses. Verify role-based permissions across transaction sequences.
Regression Testing
Add specs as your protocol evolves. Automatically verify patches don’t break invariants. Continuous verification in CI/CD pipelines.
Audit Preparation
Catch bugs before external audits. Reduce audit findings and costs. Demonstrate thorough testing to auditors.
Express intent, not implementation
Benefits
Declarative specifications describe correct behavior. No need to write custom test harnesses. [V] language makes temporal properties simple and concise.
OrCa explores thousands of test cases automatically. You define what’s correct, OrCa proves it or finds counterexamples.

Beyond traditional fuzzing
Traditional Fuzzers
Require extensive test harness code. Random exploration without guidance. Simple assertions limited to single transactions. Miss complex multi-step vulnerabilities.
OrCa’s Approach
Declarative specifications. Targeted exploration guided by properties. Temporal logic across transaction sequences. Catches vulnerabilities requiring specific multi-step setups.

Frequently AskedQuestions
How difficult is it to learn the [V] specification language?
[V] syntax is concise and intuitive. The language focuses on expressing intent, not implementation details. Examples and templates accelerate onboarding.
What types of bugs can OrCa find?
OrCa generates thousands of test cases to find violations of your temporal specifications. Common discoveries include access control bypasses, timing vulnerabilities, state inconsistencies, and complex reentrancy patterns.
How long does OrCa take to run?
Runtime depends on protocol complexity and specification scope. Typical fuzzing campaigns run 10-30 minutes, but the total length is up to the user OrCa reports violations immediately when found. Continuous integration runs fit standard CI/CD time budgets.
Does OrCa generate false positives?
OrCa reports concrete counterexamples with exact transaction sequences. Every finding is reproducible. If OrCa reports a violation, your specification is violated.
How does OrCa compare to Echidna or Foundry's fuzzer?
OrCa uses declarative [V] specifications instead of requiring test harness code. OrCa understands temporal properties across multiple transactions. OrCa provides protocol behavior insights beyond pass/fail results.
What if I don't know what specifications to write?
A: Start with protocol invariants: token supply conservation, balance consistency, access control rules. OrCa’s specification library provides templates for common patterns. Specifications evolve as you understand your protocol better.
Catch bugs before deployment
Static analysis with mathematical guarantees. Integrate in minutes.
Get started in 30 minutes / No setup required / See results immediately